What's in this post...
![]()
Last Updated on February 25, 2016 by GrahamWalsh
So you want to communicate with your Office 365 Skype for Business without having an on-premise server. Well Pexip Infinity can act as a Edge Server that can federate with Office 365.
There is an overview here and a step by step guide here on the Pexip Docs site.
However, below are the similar simple steps to get this setup and working with a DMZ deployment.
Step Zero – Planning DNS Names
If you already have your domain name in use by Office365 such as example.com, you will have sip.example.com associated with that. Now if your Pexip deployment will be using the same domain name, then it must have a sub domain so there is no conflict. For the Pexip DMZ node, you will need to use something like pex.example.com or vc.example.com. Then for the your DNS entries, you will need sip.pex.example.com and for the SIPFederationTLS you will need _.sipfederationtls._tcp.pex.example.com. You will then need an A record of sip.pex.example.com pointing to the DMZ conference node.
In the setup below, the domain name is different to my Office365 Domain so it is straightforward, but many deployments will have the same domain name.
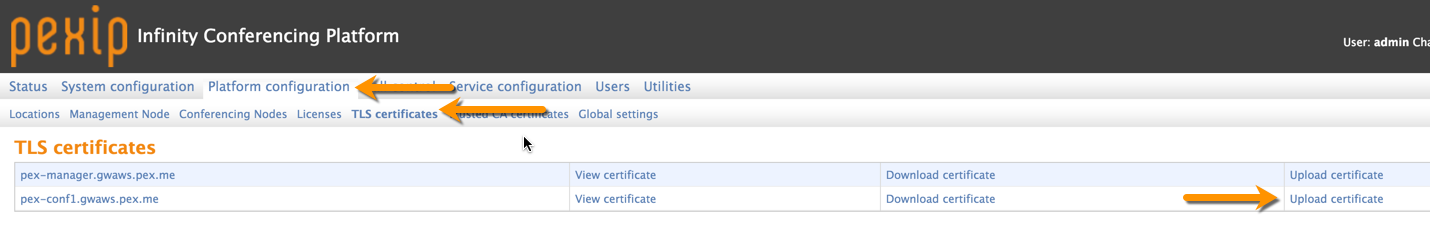
Step One – Certificates
First you need to have publicly signed certificates, you can get a trial one from www.ssl.com if you are just doing a lab setup. Just remember that the trial certificates are not SAN certificates, so the conference node SIP TLS FQDN much match the Common Name (CN) of the certificate.
First import the Trusted CA from your provider.
Then import the actual certificate for the conference node
Step Two – Configure Conference Nodes
Depending on the your certificate and number of nodes, you either set the SIP TLS FQDN as the FQDN of the conference node (as that should be in the SAN certificate) or if you only have one node and one standard certificate, you just set it to the Common Name (CN) of the certificate.
Step Three – Setup a DNS SRV Record
Depending how your DNS is managed, it may be similar to mine below where I create the SRV record.
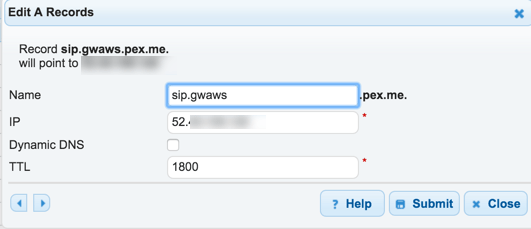
Step Four – Setup an A Record for the Conference Node(s)
Now we need to configure an A record as we’ve told the SRV record to point at sip.x.x.x in my example above. You also need to ensure you have A records for your conference nodes too.
Step Five – Test Drive it
Now you should be able to call from your Office 365 Skype for Business account to a Virtual Meeting Room or for example, a user could browse to the conference node and utilise WebRTC and make a call to the Office 365 Skype for Business user.
I’ve put together a video overview of the platform installed in AWS and with two simple gateway rules to allow Skype for Business interoperability.