![]()
Last Updated on October 21, 2020 by GrahamWalsh
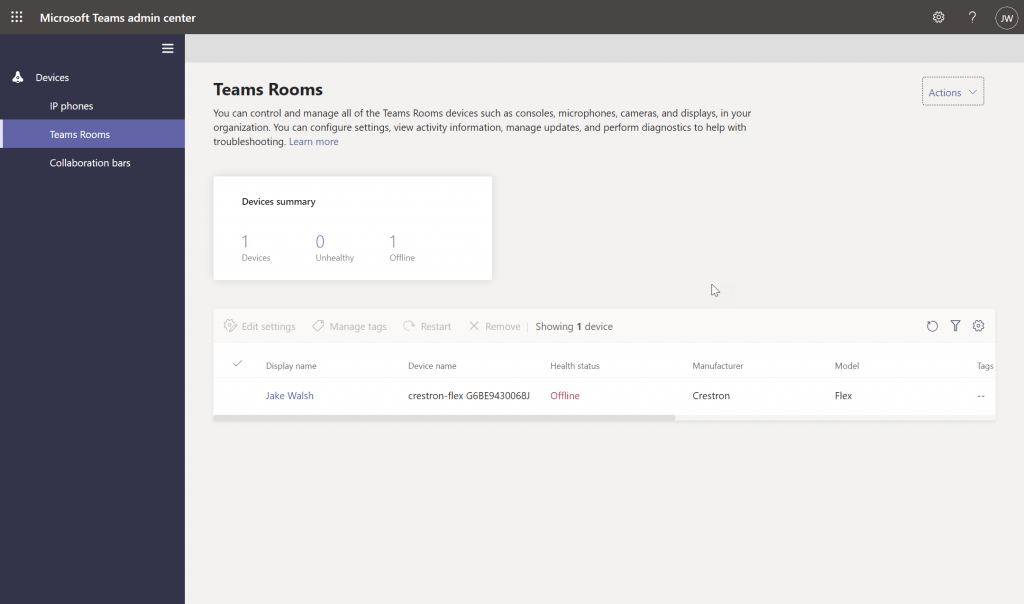
Many organisations may want to outsource their Microsoft Teams Device Administrator role to a third-party. However, in the past, they would need to assign them full rights to their Teams Admin Center (TAC) as you can see below. This is obviously not ideal as someone who has a login could make unnecessary changes.
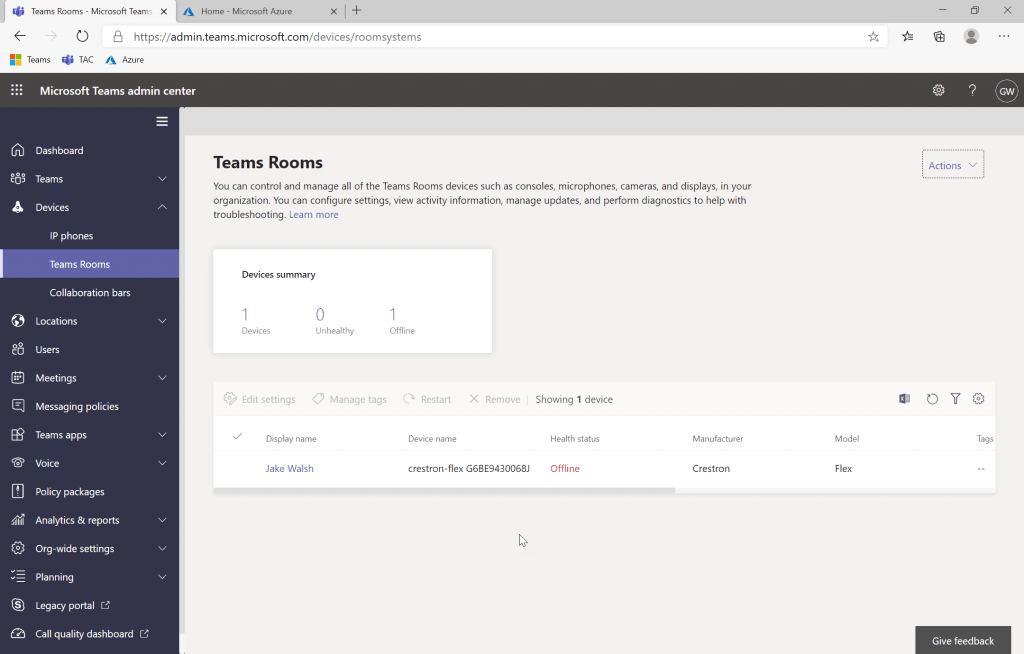
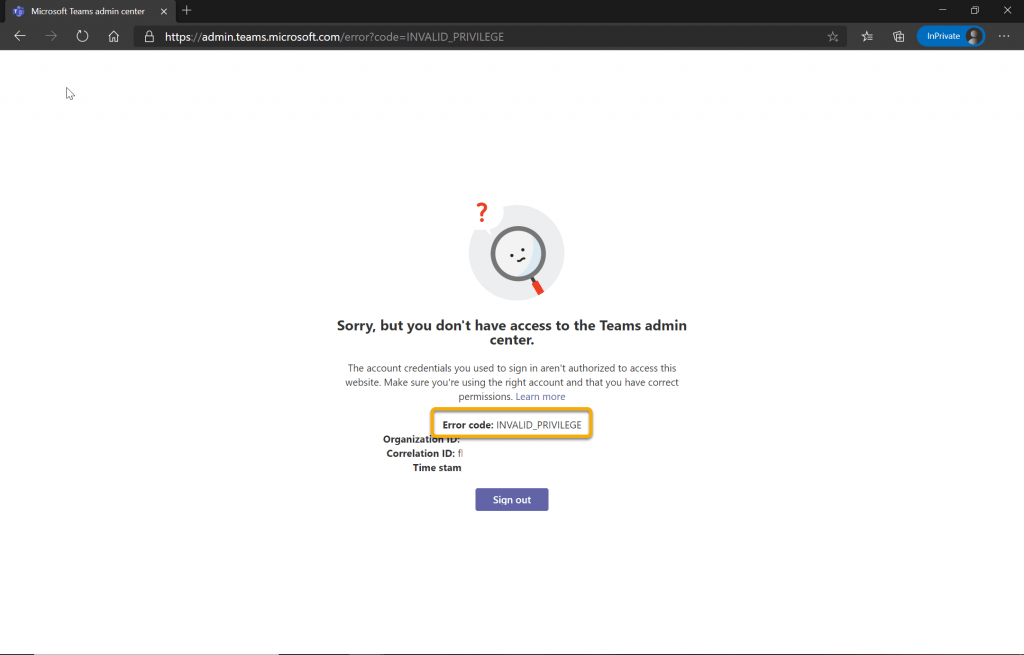
Fast Forward to the new Teams Devices Role which needs to be setup in the Azure Active Directory portal. If I’m a standard user and try and login to the TAC, I see the error below.
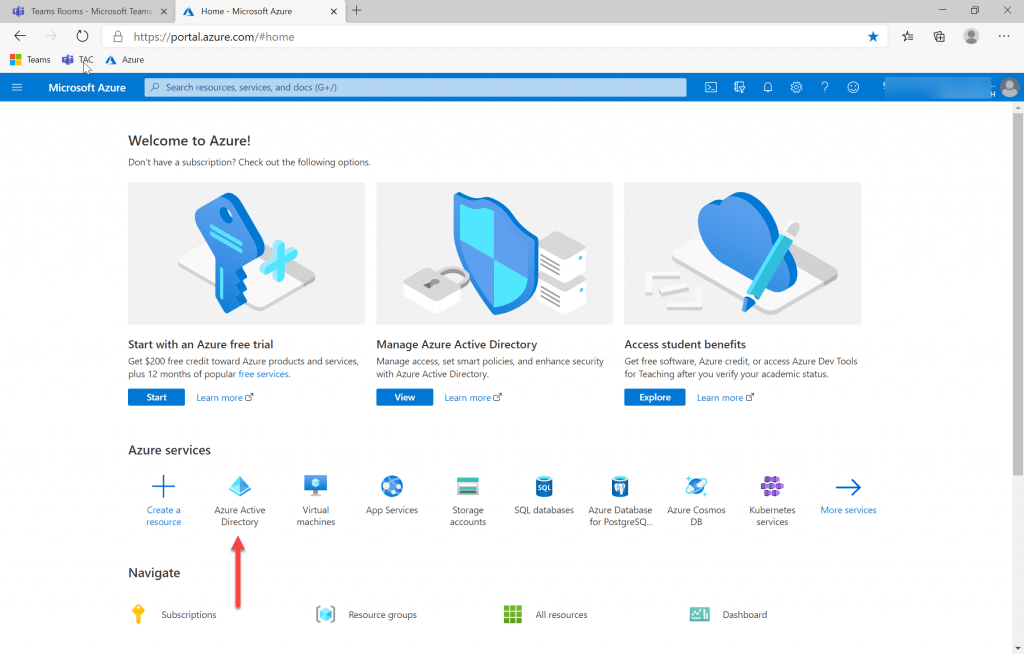
Firstly, I need to login to Azure Active Directory (AAD) via https://portal.azure.com and then go to AAD. From there I need to go to Roles and Administrators.
Now navigate to Roles and Administrators and search for Teams. You will now see the list of roles available for Teams. Next click on Teams Devices Administrator.
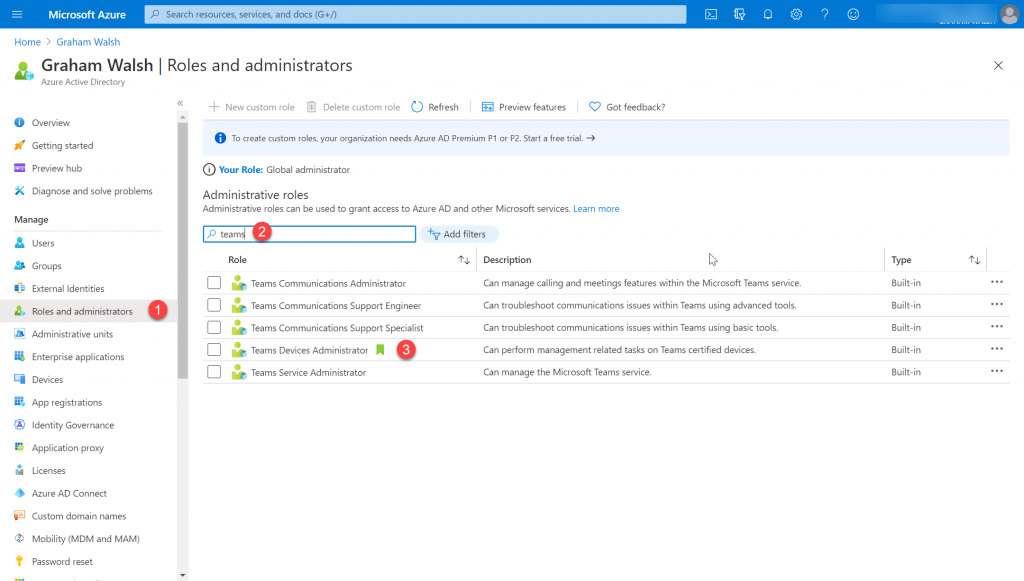
Now we can add someone to this role and I’m going to select Jake for this role as that is who tried to login earlier at the start of this post.
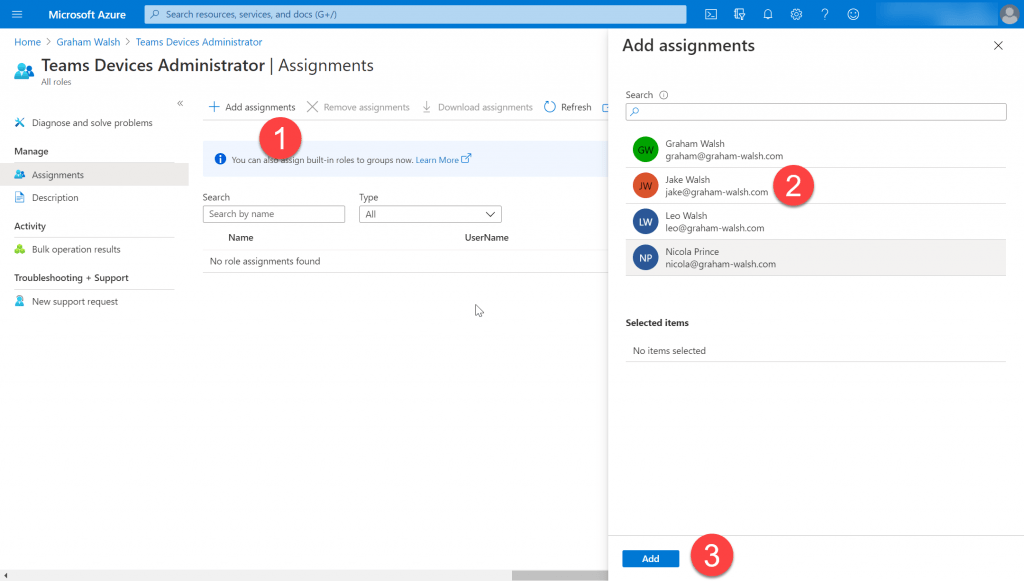
Once the role has been assigned, the user trying to login should log out, close their browser and log back in. The good news is that they should not see an error but instead see the just the Teams Devices as promsied.
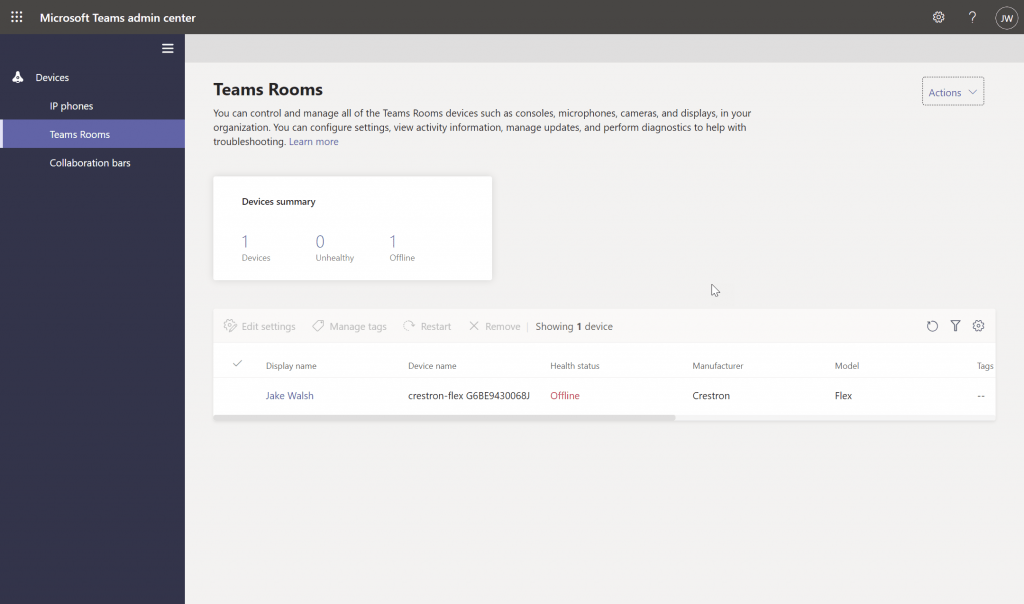
Now you can safely setup an account for someone to login and remotely manage and configure your Microsoft Teams Rooms. New features in the TAC include the ability to turn Guest Join Access for Zoom and Webex on and off.
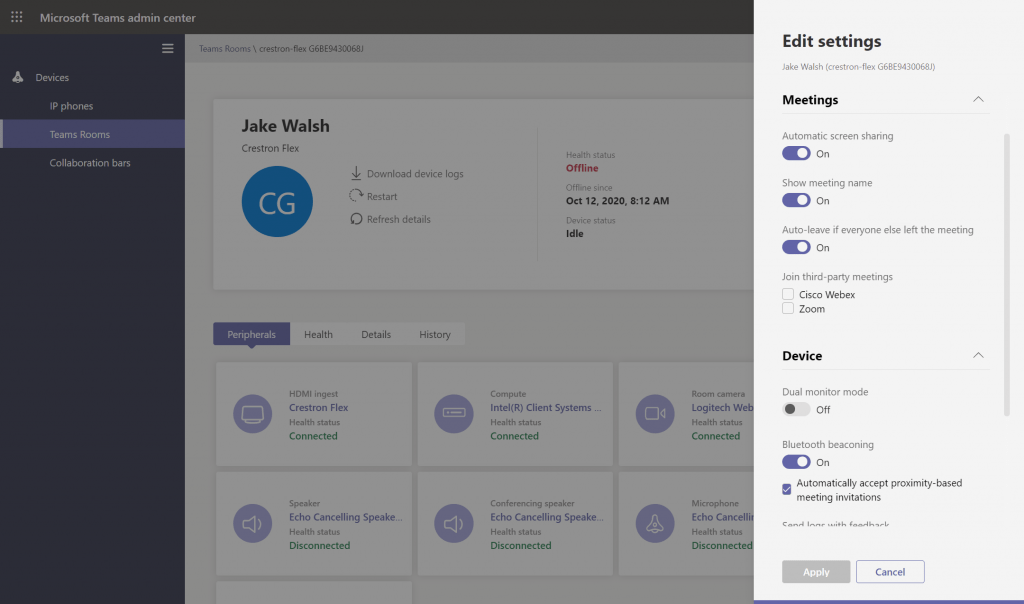
One thing to note here is that the Teams Devices Administration role does not allow access to call logs. This can be a good and bad thing. It means third-parties cannot see who has been calling who and what their display name etc is. However, it then prevents them from analysing why a call dropped for example. That would need to be done by someone who has the Teams Communications Administrator role.
Also this role will be available to setup in the Microsoft 365 portal too soon.
Any questions, let me know below.